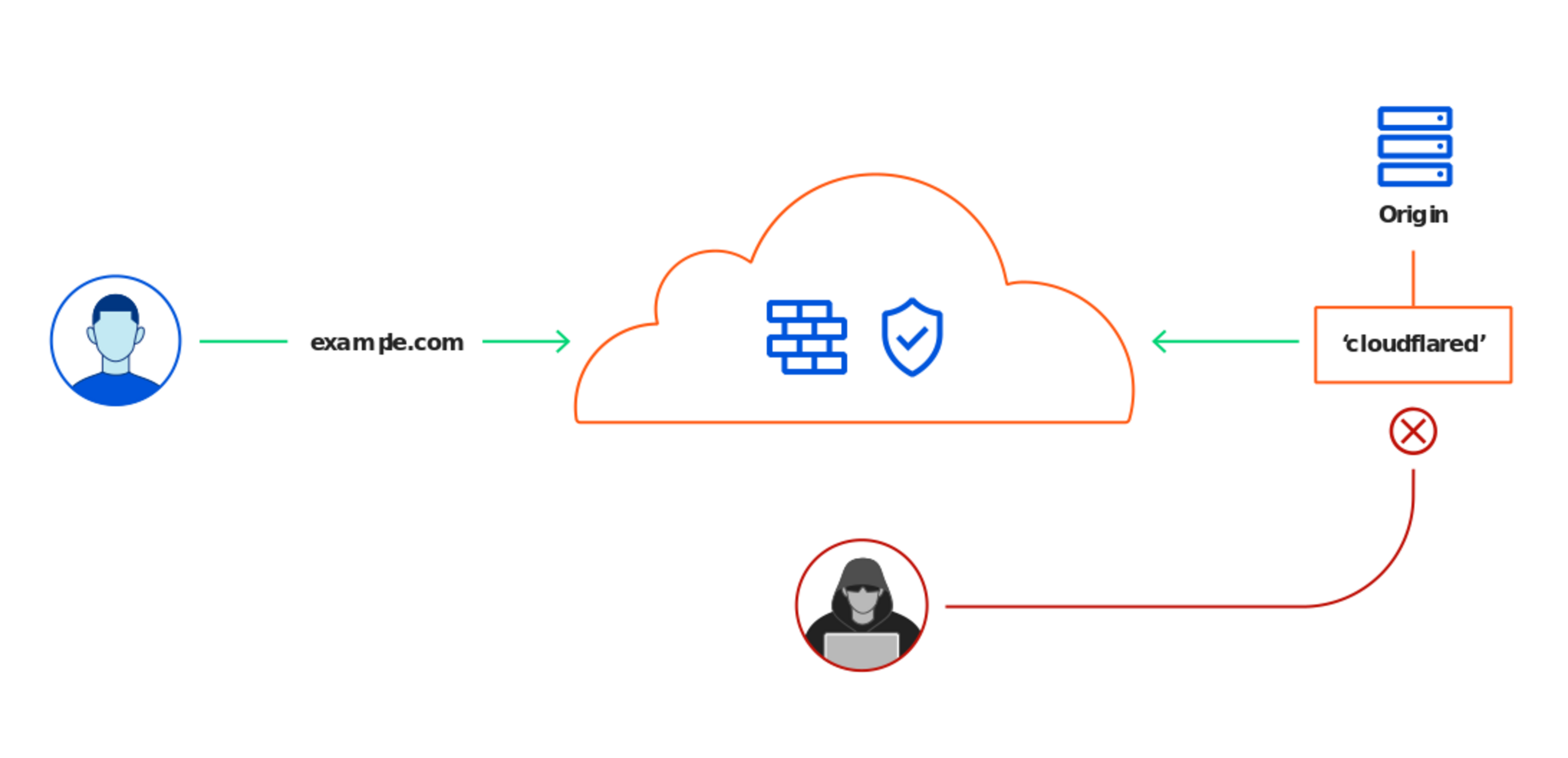
Attackers use Cloudflare Tunnel to proxy into victim networks
5 (325) · € 17.99 · Auf Lager
Hackers Abuse Cloudflare Tunnels To Bypass Firewalls
Tunnel · Built with Workers · Cloudflare Workers®
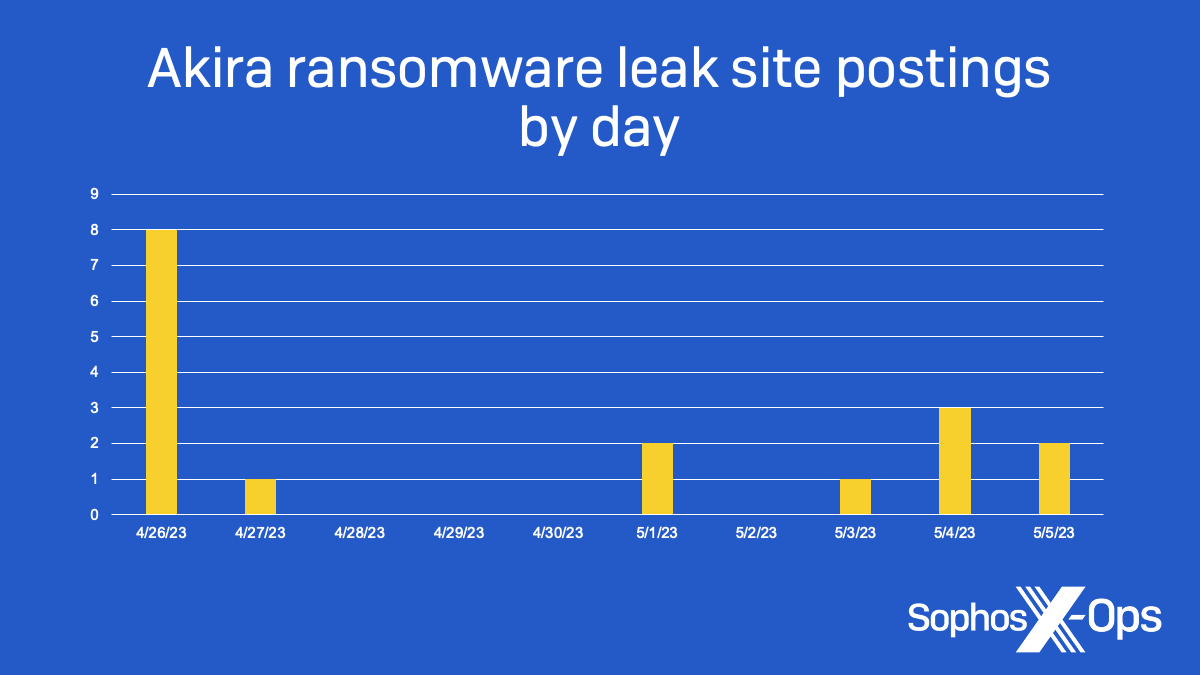
Akira Ransomware is “bringin' 1988 back” – Sophos News
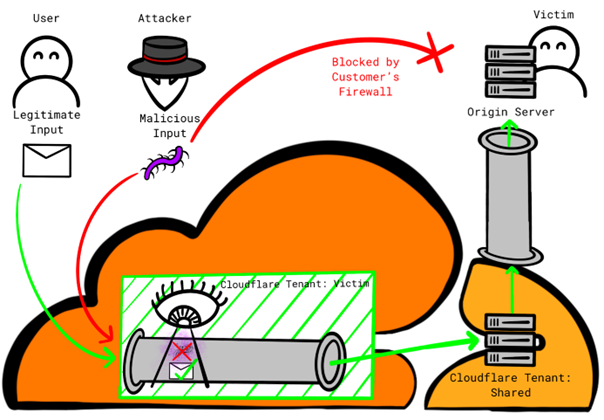
Using Cloudflare to bypass Cloudflare – Certitude Blog
How to stop DDOS attacks? Other than using CloudFlare or another reverse- proxy protection setup, what measures can I take to stop those attacks - Quora
Beat - An Acoustics Inspired DDoS Attack

New Memento ransomware uses password-protected WinRAR archives to block access to the files

X-Pro: Distributed XDP Proxies Against Botnets of Things
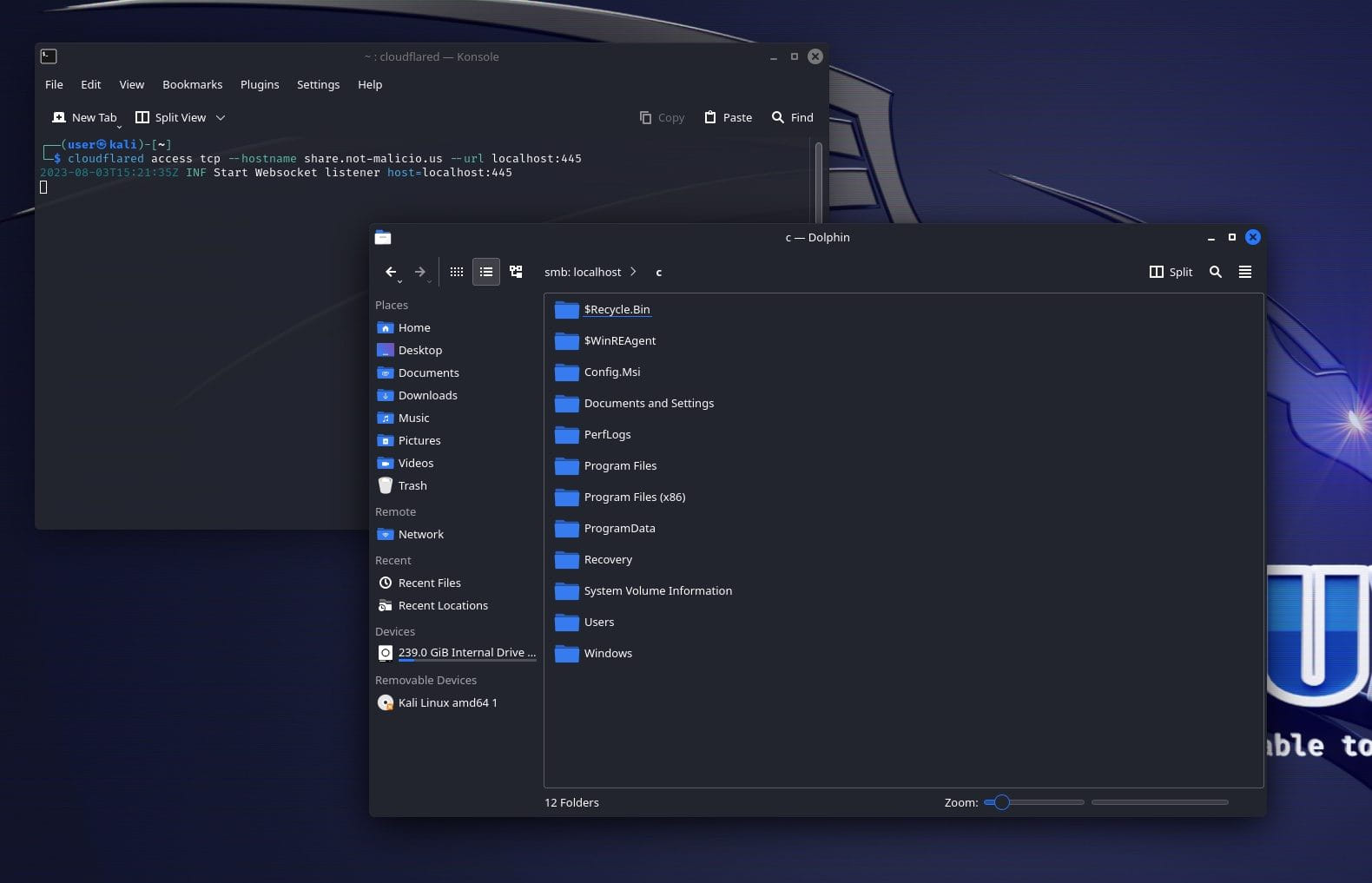
Hackers increasingly abuse Cloudflare Tunnels for stealthy connections

Attackers Use Cloudflare Tunnel to Proxy Into Victim Networks - Kepler Safe
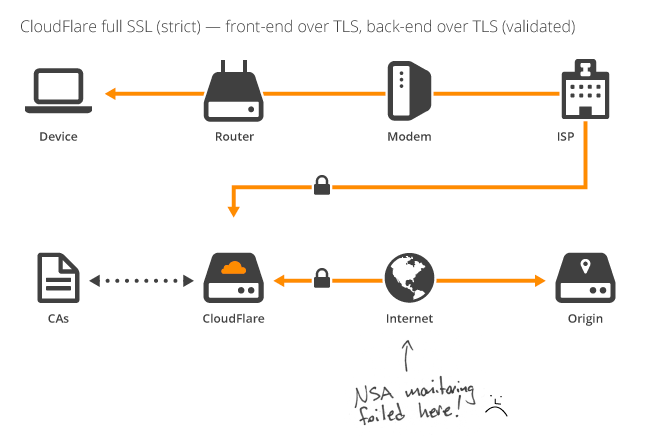
Introducing Strict SSL: Protecting Against a On-Path Attack on Origin Traffic
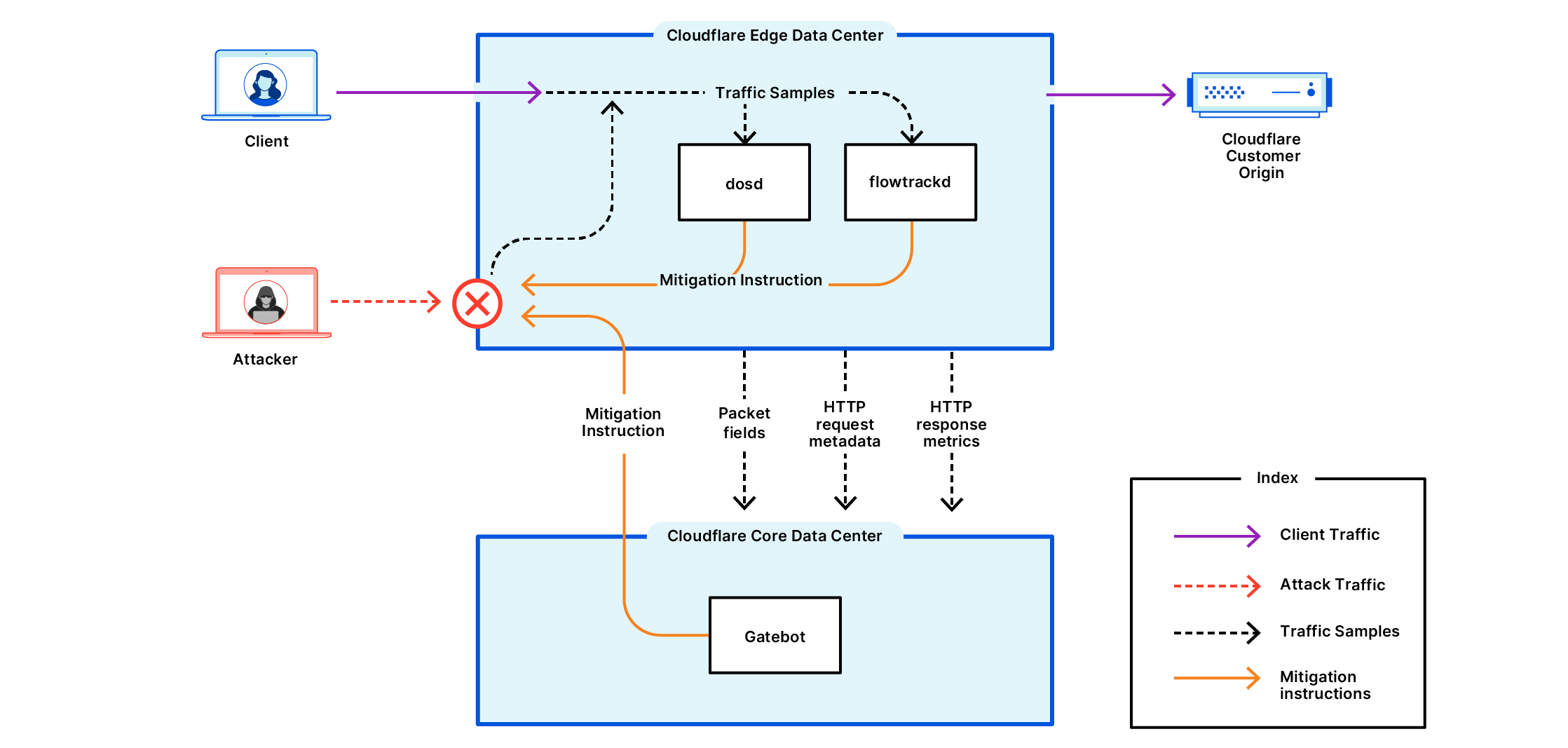
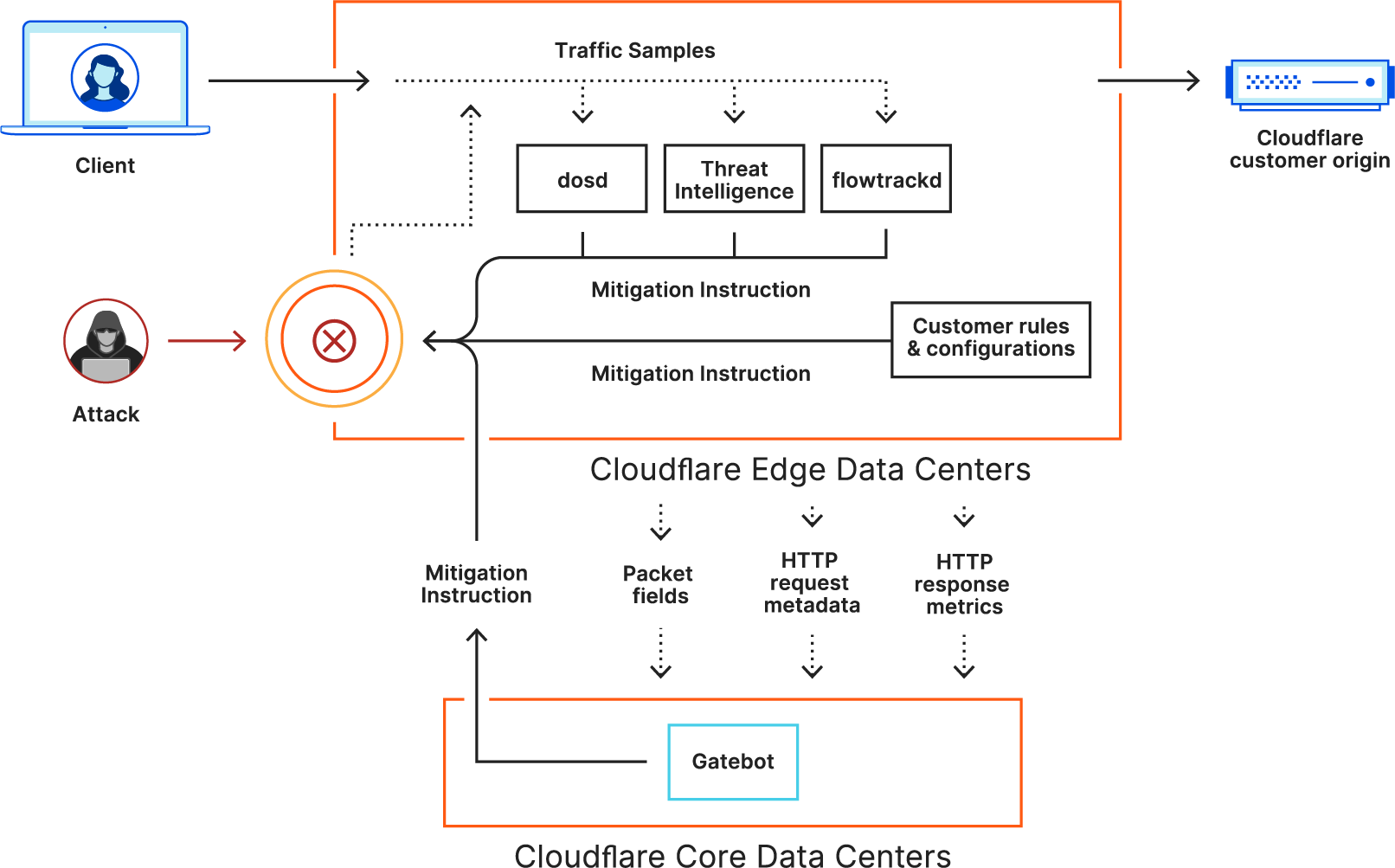
A deep-dive into Cloudflare's autonomous edge DDoS protection
Securely access home network with Cloudflare Tunnel and WARP

Security Key MFA Stops Phishing Attack on Cloudflare - Rublon












